
What is Vault?
Vault is a tool created by HashiCorp that provides “Secure, store and tightly control access to tokens, passwords, certificates, encryption keys for protecting secrets and other sensitive data using a UI, CLI, or HTTP API.”
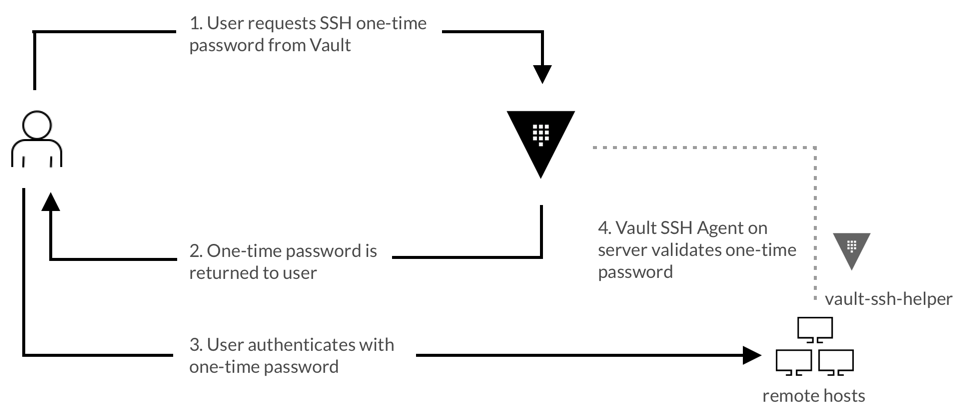
One common use of vault is to leverage the OTP token generation paired with the ssh engine to create a secure authentication solution for SSH access to servers.
If all of this is alien to you, then HashiCorp has excellent documentation and you can check out this link for a much more in-depth explanation of this. Because of this, I am not going to go into detail on what this is and how to set it up.
TL;DR
Vault OTP ssh is set up by using a custom PAM configuration on the server, this same PAM configuration can be used for sudo to have OTP sudo access instead of configuring passwords for users.
Where does sudo come into this?
For people that are familiar with Vault OTP SSH and are using it on their servers currently, you probably have seen this set of instructions before:
https://learn.hashicorp.com/vault/secrets-management/sm-ssh-otp
Looking at this specific part of the above instructions:
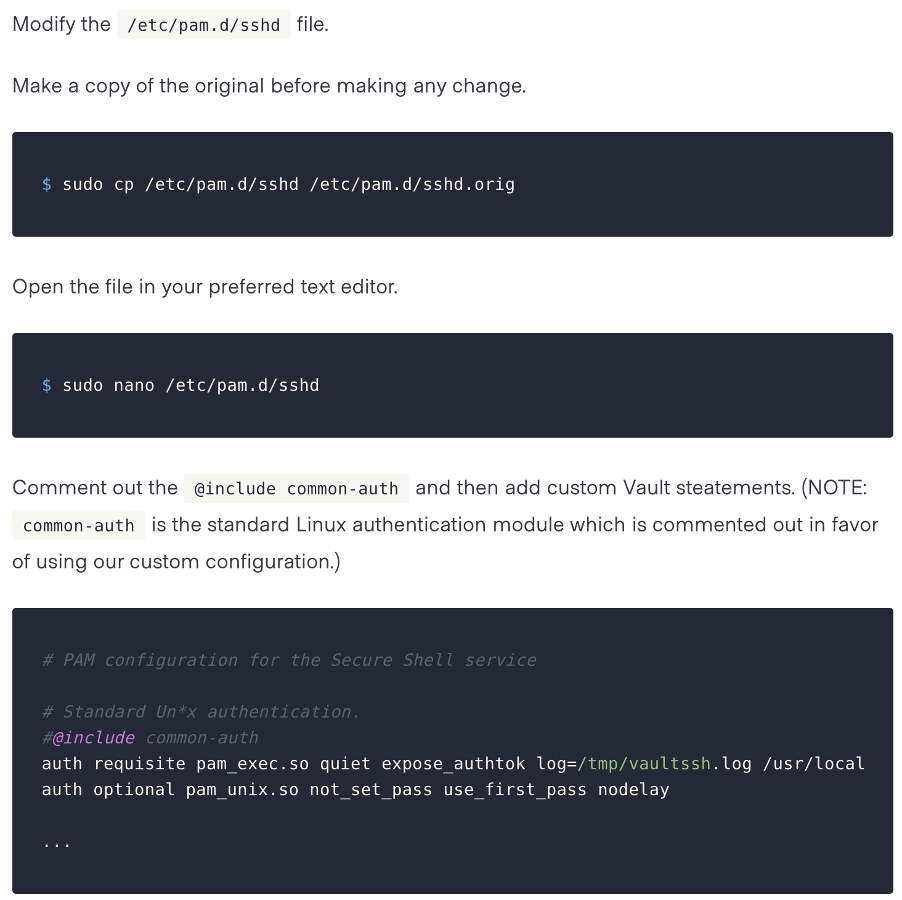
So this provides a great password-less method of sshing into your servers, but once you are in as your user on the server, a common issue is engineers setting the NOPASSWD option for sudo because the users are not provisioned with a password or they still have to manage user passwords in order to sudo. With these two options commonly being adopted, there had to be a better option between the insecure and the redundant.
The fact vault used PAM sshd module for ssh authentication, I figured that there was no reason you couldn’t do the same thing for the sudo module. So I decided to try and see, taking a look at the sudo PAM module in /etc/pam.d/sudo:
#%PAM-1.0
auth include system-auth
account include system-auth
password include system-auth
session optional pam_keyinit.so revoke
session required pam_limits.so
I modified it in a similar manner as the instructions implied for ssh. I added the auth requisite and auth optional lines pointing to the vault-ssh-helper binary.
#%PAM-1.0
auth required pam_sepermit.so
auth requisite pam_exec.so quiet expose_authtok log=/tmp/vaultssh.log /usr/local/bin/vault-ssh-helper -config=/etc/vault-ssh-helper.d/config.hcl debug
auth optional pam_unix.so not_set_pass use_first_pass nodelay
account include system-auth
password include system-auth
session optional pam_keyinit.so revoke
session required pam_limits.so
session include system-auth
Boom! It worked like magic. Generate one token to get on the server and then when you need to sudo you can generate another token and enter it at the password prompt.
[test@myserv ~]$ sudo -s
[sudo] password for test:
[root@myserv ~]$
This is nothing mind-blowing, but I believe it is a slick way of maintaining password-less authentication on servers for both SSH and sudo. Just an extension to the existing functionality provided by vault.
Hi!
Your tutorial was very good, to the point and it worked perfectly. Thanks for sharing your work…